Security, Risk &
Governance
iManage Threat Manager & Security Policy Manager
Organizations in legal, accounting, finance and other industries are facing new and sophisticated forms of security threats that require innovative technology to protect sensitive information. With rising customer demands and regulatory requirements, companies are also under pressure to secure and manage client information to a higher standard. iManage delivers need-to-know security, protects sensitive information from phishing and internal threats and supports ethical walls and client audit requests, all without burdening the user with additional steps and work. Using iManage, organizations work safer with products that govern and secure their critical information.
Videos
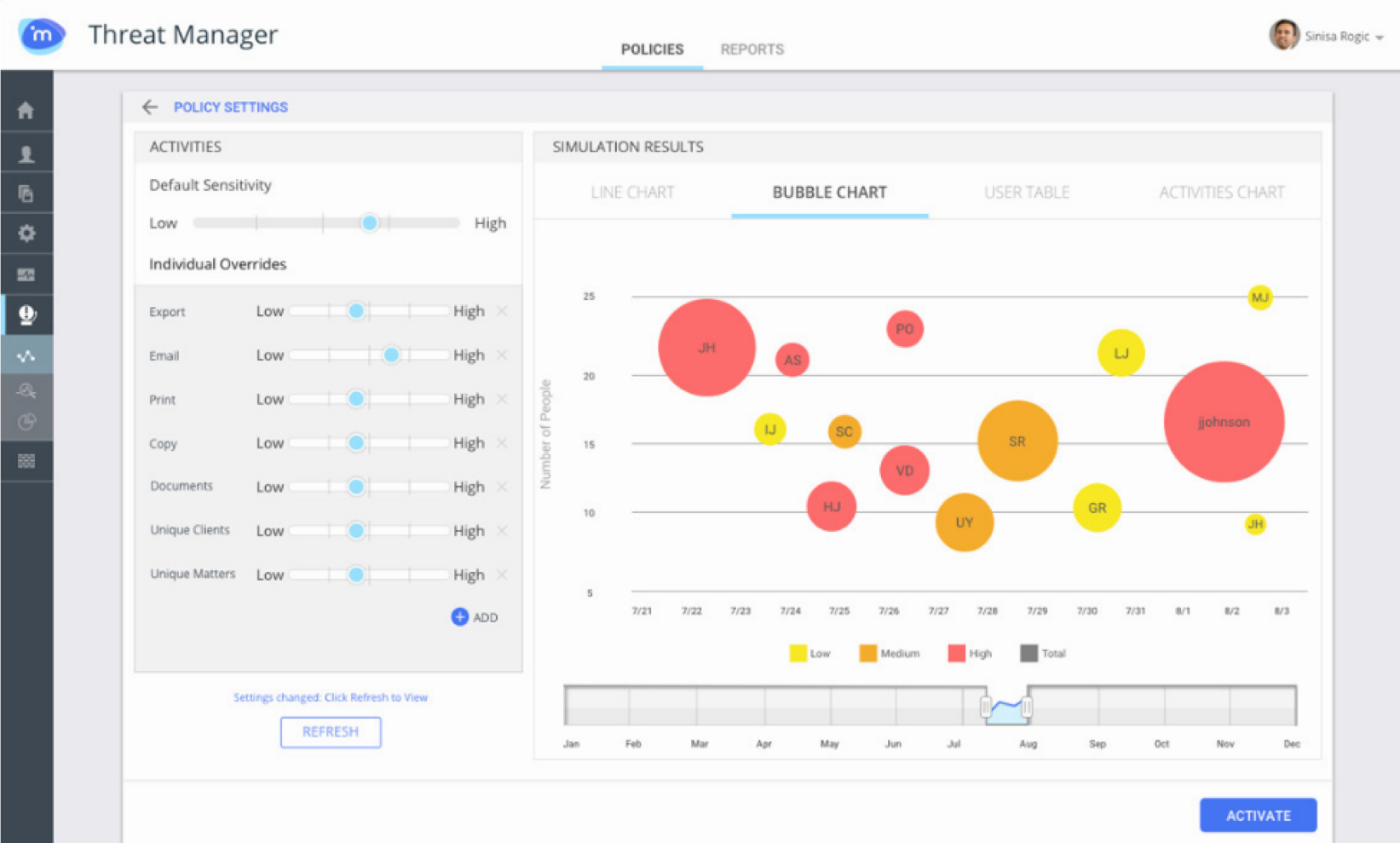
iManage Threat Manager
Leverage machine learning to improve threat detection – an advanced solution to meet the needs of CIOs, CSOs and compliance personnel to protect data from external and internal threats
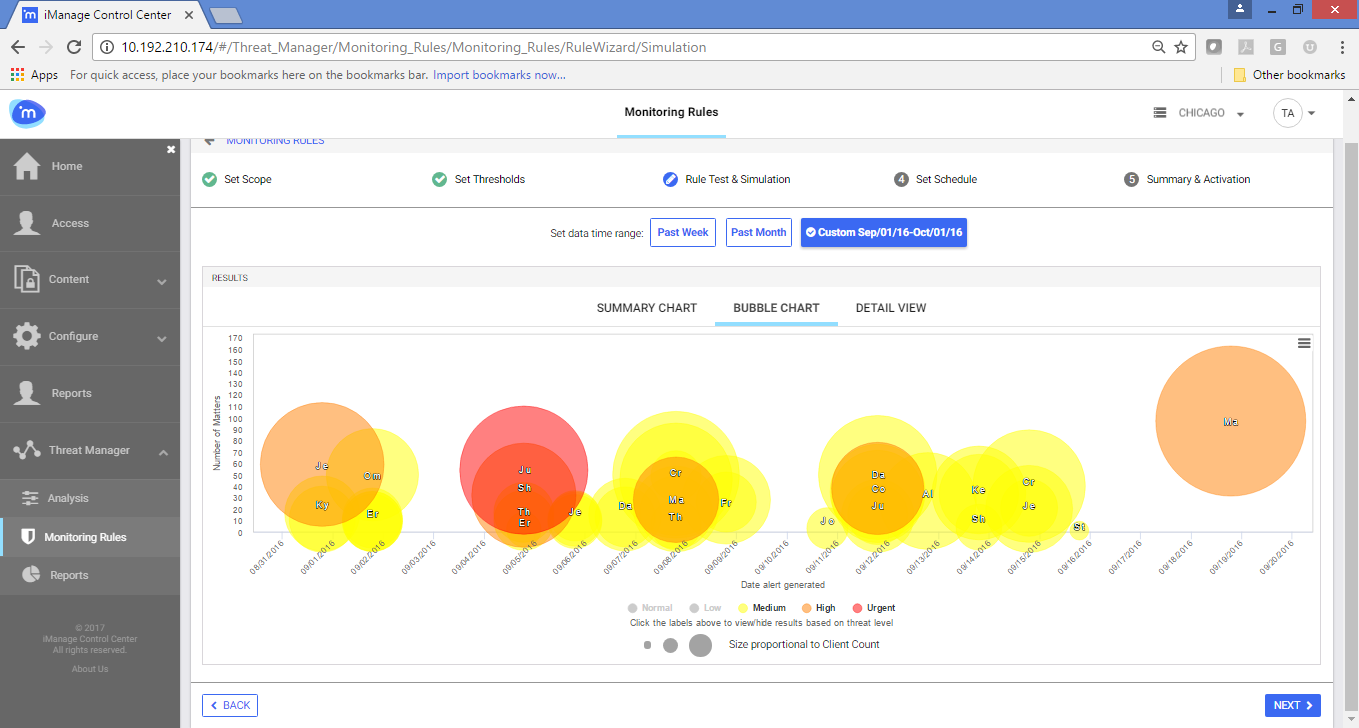
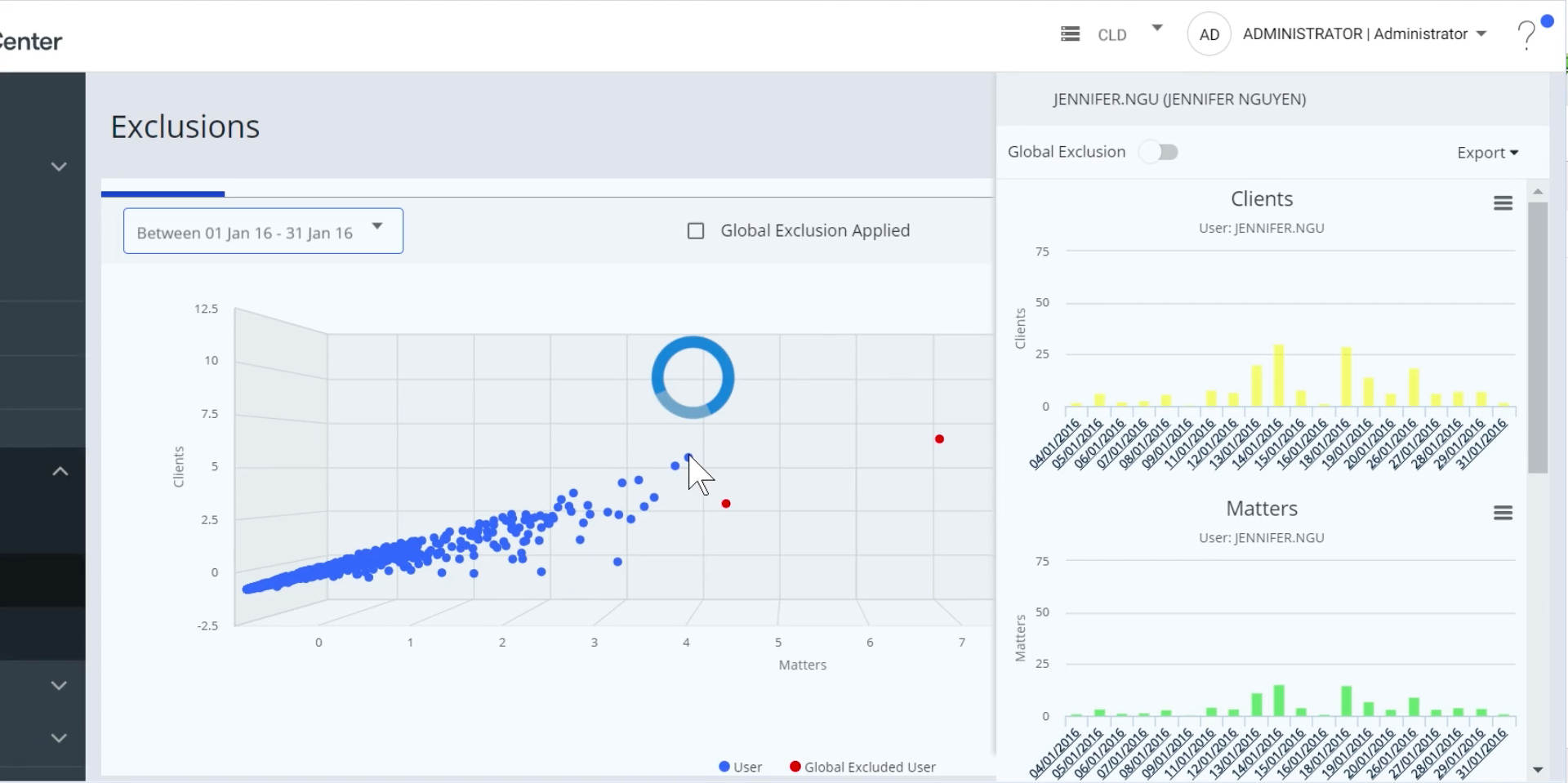
iManage Threat Manager is designed to meet the needs of CIOs, CSOs and compliance o icers looking for advanced solutions to protect sensitive data. Threat Manager, leverages historical and contextual information in the iManage system to provide faster identification of both external and internal threats, and avoids pitfalls such as “false positives” that plague many other approaches. iManage Threat Manager delivers threat detection, monitoring, investigative capabilities, alerts and reporting to protect sensitive information in your iManage system 24/7 across any device, anywhere.
With historical and contextual information in the iManage system, you can identify external and internal threats faster, while avoiding the trap of false positives and other methods. Provides threat detection, monitoring, investigation, alerting, and reporting capabilities to continuously protect sensitive information in iManage 24/7 on any device, anytime, anywhere.
iManage Threat Manager uses state-of-the-art machine learning to understand the unique context of professional operations for the highest value data: practice areas, customers and projects. For example, access without a time charge, or access to expertise outside the case. iManage Threat Manager provides 24/7 continuous threat protection that can be discovered and removed as soon as a threat occurs.
![]() Comply with client regulations
Comply with client regulations
![]() Detect threats with the highest levels of accuracy
Detect threats with the highest levels of accuracy
![]() Comprehensive investigative tools, reports and process automation reduce the time and effort to neutralize a threat
Comprehensive investigative tools, reports and process automation reduce the time and effort to neutralize a threat
![]() Easy to deploy, support and integrate with -available on the cloud or as an appliance (on premises)
Easy to deploy, support and integrate with -available on the cloud or as an appliance (on premises)
![]() 24/7 Continuous threat protection
24/7 Continuous threat protection
Key Benefits
1
Detect sophisticated threats from internal or external actors
2
Reduce the risk of data breaches
3
Accelerate time to investigate
fraudulent behavior
4
Reduce false positives, ensuring that precious resources are spent on the alerts that are most likely to be fraudulent
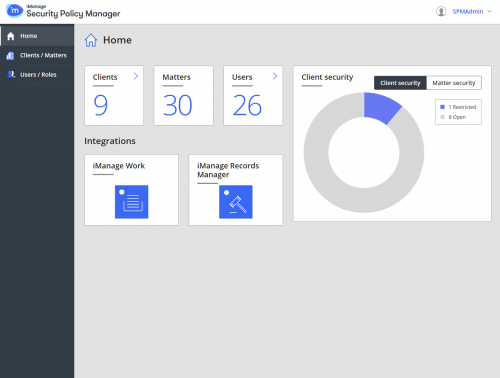
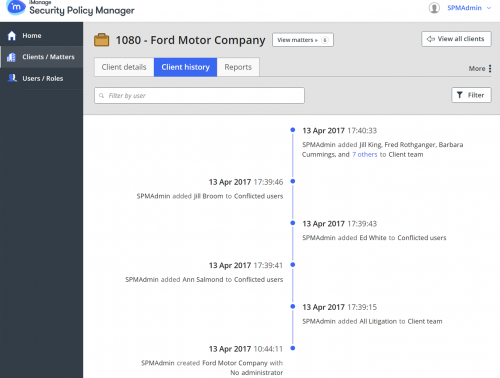
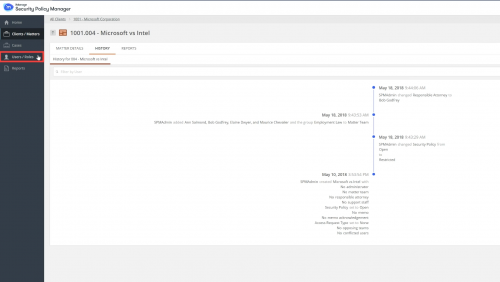
iManage Security Policy Manager
Global Security Policy Management for Today’s Security Challenges
Securing sensitive content on a need-to-know basis and segmenting other content appropriately within the firm are critical parts of any strategy to limit the exposure and reputational damage that a breach can bring. A new approach to data security is needed and with it so ware that can handle the volume and complexity of security policies is required.
iManage Security Policy Manager meets modern security challenges with no impact to firm productivity. Security Policy Manager allows you to manage your global security policies, including ethical walls and barriers, at scale to meet today’s increasing client demands. Security Policy Manager delivers data protection without inconveniencing professionals by getting in the way of how they want to work.
As a product for the delivery of Ethical Walls, enabling users to move away from relevant content and realizing the lawsuits that could not be filed, document access rights and billing activities can be used to automatically exclude users from home projects. Allow the law firm to pick up customers and homes at the same time.
![]() Instant protection with no-refiling or re-indexing of Work content
Instant protection with no-refiling or re-indexing of Work content
![]() Secure sensitive data to those who need-to-know
Secure sensitive data to those who need-to-know
![]() Segment data in multiple ways
Segment data in multiple ways
![]() Modern intuitive user experience
Modern intuitive user experience
![]() Multiple security policy types
Multiple security policy types